Information Security
Information Security Policy
To maintain information confidentiality, completeness, availability, and legitimacy, and protect information assets against internal or external man-made, intentional, or accidental damages that affect corporate operations or harm corporate interests, Ability has established its information security policy to serve as the standard to implement various information security measures; the descriptions are as follows:
ISO 27001 information security management system
To reinforce information security protection, the Company comprehensively promoted the introduction of the information security management system in 2012 and obtained the ISO 27001 information security management system (ISMS) certificate in August 2013. The Company continues to advance its cybersecurity system structure, requires employees to implement information security management specifications, and build a comprehensive information security protection force via information assets and risk assessments, monitoring operating impact analysis, business continuity drills, and other systems to include information security awareness and concepts in the corporate culture and take steps forward to building the zero trust network structure.
Information security organization
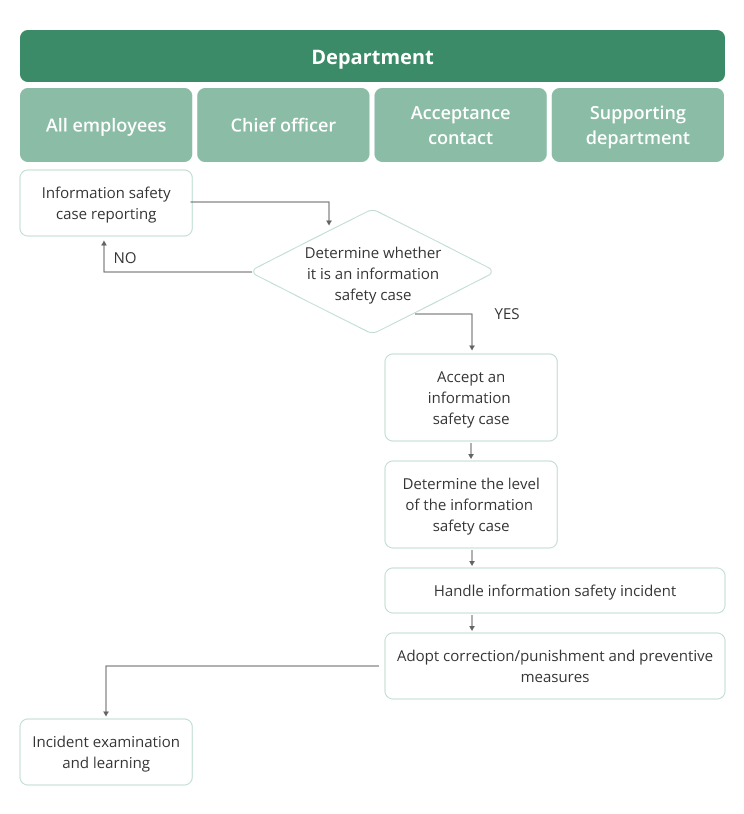
The Company particularly established an information safety processing team for corporate information safety, regularly convened management review meetings, and established and examined information safety management targets and policies. To effectively promote information management policies, the project team, safety prevention team, crisis management team, information safety audit team, and supplier promotion team are established under the information safety organization, comprising senior management personnel of different functional departments to ensure the continued stable operation of the information management system.
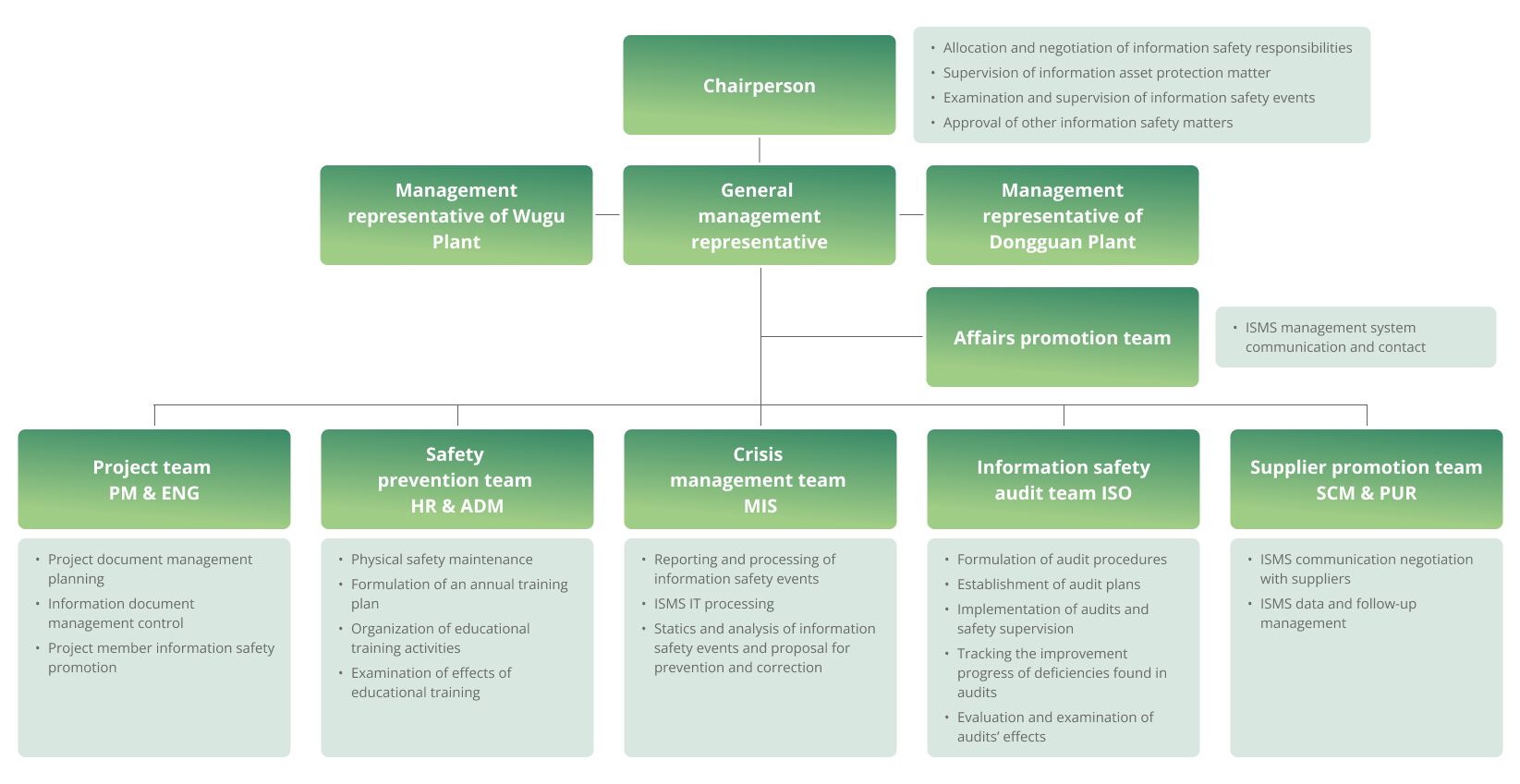
We comply with information security policy requirements via the introduction of the ISO 27001 information security management system and regularly carry out information security promotion and employee information security educational training. Internal and external professional auditors and the organization carry out audits of the information security management system each year, evaluate the information operating status, risk control, and event improvement, and report to the information security processing team to control and minimize information security risks.
Information security event reporting and response system

.jpg)